Does your Raspberry Pi need a shield against the digital storm? Absolutely! In today's interconnected world, a firewall is not just a recommendation, it's a necessity, especially for devices like the Raspberry Pi that are often exposed to the internet or local networks.
The world of Raspberry Pi projects is vast and varied. From home automation hubs to media servers, these little computers pack a powerful punch. However, with great power comes great responsibility, especially when it comes to cybersecurity. Every Raspberry Pi, connected to a network, is a potential target. It's like leaving a door unlocked in a bustling city; you're inviting trouble, even if you don't realize it.
The heart of this protection lies in the software that governs incoming and outgoing network traffic. Raspberry Pi OS, the most common operating system for these devices, comes equipped with a powerful, albeit complex, tool called `iptables`. This is the default, built-in firewall on most Linux systems, and it's capable of incredibly granular control over your network. However, configuring `iptables` can feel like navigating a labyrinth for the uninitiated.
- Unlocking The Potential Of Aagmal Tech Your Ultimate Guide To Digital Innovation
- Wasmo Mia Khalifa Telegram A Deep Dive Into The Viral Sensation
Fortunately, there's a more user-friendly solution: `ufw`, short for "Uncomplicated Firewall." Think of `ufw` as a translator, making it easier to communicate with the underlying `iptables` engine. It simplifies the process of setting up rules to allow or deny network traffic, offering a balance between robust security and ease of use. Think of it as a user-friendly interface on the very complex iptables.
The beauty of the Raspberry Pi is its versatility. It can be tailored to a wide array of tasks. Perhaps you're setting up an SSH server for remote access, hosting a personal website, or running a service that needs to accept incoming connections. Without a properly configured firewall, these services are vulnerable.
When you first boot up your Raspberry Pi, it's not a wide-open invitation to the internet. By default, the operating system blocks many incoming connections to specific ports, a built-in layer of security. But, this default behavior may hinder your project, as it can prevent you from accessing the services you're running. So, you need to be careful about the configuration
- Skymovieshdvideo Your Ultimate Destination For Streaming Movies
- Unveiling The Truth About Mallu49c9m A Comprehensive Guide
Let's get practical. To install `ufw`, you'll use the command line. It's the gateway to all things Linux. You'll type a simple command, and in a matter of moments, `ufw` will be ready to help you secure your Pi. It is a front-end for managing firewall rules. It sits on top of `iptables`, the powerful but complex firewall configuration tool found on Linux systems. Using `ufw` simplifies configuration without sacrificing security.
The process of setting up a firewall requires careful consideration. You need to strike a balance between security and accessibility. You want to block malicious traffic but still allow legitimate connections to the services you need. It involves defining rules, which specify what traffic is allowed and what is blocked. It is all about creating a system that protects the device from unauthorized access while also allowing it to function as intended.
The configuration isn't just about preventing unwanted access. It's about fine-tuning the flow of data to optimize the function of the Raspberry Pi. Think of it as a traffic management system. Well-configured rules ensure that the necessary traffic can pass through, and the system remains secure. Establishing these rules requires precision and a clear understanding of the services you want to provide. If, for example, you intend to host a website on your Pi, you'll need to configure the firewall to allow incoming connections on port 80 (for HTTP) and port 443 (for HTTPS).
Before enabling `ufw`, it's essential to configure the rules. The first thing is to ensure that you have properly set up the firewall to prevent it from disrupting your network. Once the firewall is enabled, it's not an easy task to change the rules, so it is wise to be careful from the start. This ensures that your Pi remains accessible and functional while being protected. You can customize settings to meet your specific requirements.
Securing your Raspberry Pi with a properly configured firewall is non-negotiable. It acts as the first line of defense against cyber threats, and it can block access. It will monitor the incoming and outgoing traffic and protect your device. A well-configured firewall is crucial for protecting against unauthorized access and data breaches.
There are several tools and methods to help you accomplish this. `Ufw` is an excellent starting point for its simplicity. However, if you need more granular control, you can delve into the complexities of `iptables` directly.
For more advanced users, it's possible to use the Raspberry Pi itself as a firewall for an entire network. This typically involves adding an additional network card and configuring the Pi to route traffic between the internal and external networks. With the `iptables` or `ufw` tool, you could control the flow of data and protect your entire network from unwanted access.
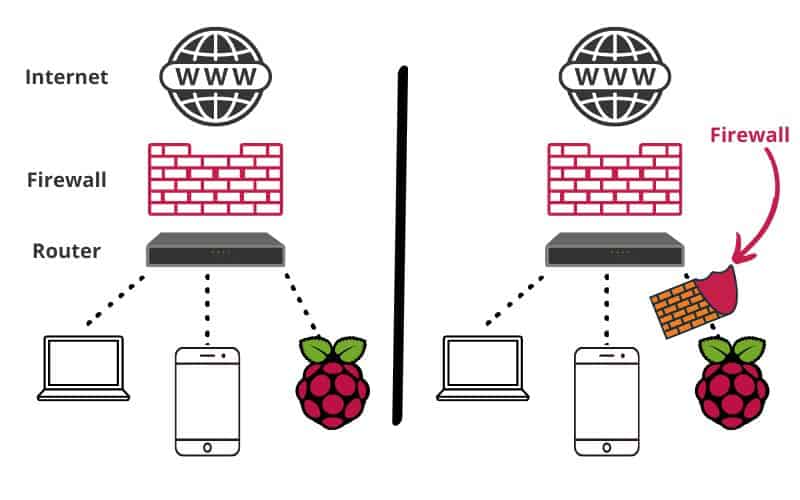
The Raspberry Pi, with its versatility and affordability, offers a powerful platform for various projects. One of these is its ability to act as a firewall, securing the network. Think of it as a digital gatekeeper, diligently managing the flow of data in and out of the network.
In some cases, setting up a Raspberry Pi firewall to protect all devices in the home network is useful. This can be achieved by adding an additional network card, such as a USB 3.0 gigabit wired network card, and configuring it as `eth1`. In that case, you will need to provide the IP address information.
Firewalls are essential in modern computing. They act as a crucial component of any computer's security system. They help protect against unwanted access and malicious attacks. They filter network traffic based on predefined rules, deciding which data packets are allowed to pass through. Therefore, a firewall becomes a barrier between connections and your Raspberry Pi. Without a firewall, the device becomes vulnerable to attacks.
When you're using the Raspberry Pi for networking, you may encounter scenarios where you need to control network traffic. By setting up a firewall, you can control and protect network traffic. It gives an extra layer of security. For example, consider a home network with multiple Raspberry Pi devices. By using a Raspberry Pi as a firewall, you can add an extra layer of security, and gain insight into your network traffic, which will ensure smooth operation.
For more advanced configurations, there are specialized tools such as FireMyPi. FireMyPi provides a configuration tool designed to help you configure and install the IPFire firewall for your home network on a Raspberry Pi. It can be used to create a micro SD card installation that will boot up and run on your Raspberry Pi out of the box.
The basic principle is simple: allow what you need, block everything else. This is where the configuration of your firewall comes into play. It is all about determining which connections are legitimate and should be allowed and which are malicious and should be blocked. The goal is to balance accessibility and protection.
As you work with the Raspberry Pi, you might find yourself in a situation where you want to access specific sites from a private network. A well-configured firewall provides you with the flexibility to achieve this securely. You can create rules to allow access to specific sites or services.
Configuring a Raspberry Pi firewall is not a task that can be completed once and forgotten. It's an ongoing process of monitoring and adapting. It's about making sure that the firewall stays up-to-date with new threats. With continuous maintenance, you can maintain the highest level of security.
To ensure everything works correctly, you will need to configure the `ip` address of the network card, fill in the router's `ip` address as the gateway, and provide information for things like DNS servers. You will need to set passwords, network configuration, and other preferences.
Ultimately, the steps involved in setting up a firewall include installation, configuration, and rule management. When the firewall is installed, you will need to set it up to balance accessibility and protection. This means you have to carefully establish firewall rules and enable them using the command-line interface.
Given the growing popularity of the Raspberry Pi, it's imperative to take security precautions to protect your device from unauthorized access and data breaches. A firewall is a key component to protecting any device exposed to the internet. Installing a firewall will allow you to protect your device and keep the malicious actors out.
The configuration of a firewall can be complicated. It will block all incoming connections to certain ports. It requires understanding the network and the services you intend to use. It will act as a barrier between connections and the device, such as your Raspberry Pi. Without a firewall, someone can attempt a connection to your Raspberry Pi on any port that has software listening on.
In the end, your security is the priority, so you have to consider the options available and implement a security system. The right firewall can significantly enhance the overall security posture of your Raspberry Pi and the network it is part of. So it is essential to secure your Raspberry Pi from unauthorized access, and that is only possible with a properly configured firewall.
- Unveiling The Truth Behind Mallu49cim A Deep Dive
- Mia Khalifa Telegram The Ultimate Guide To Her Journey And Presence